What is a Website Safety Checker?
The Website Safety Checker by Sitechecker is designed to evaluate your site’s security. It utilizes Google Safe Browsing Checker to provide comprehensive details about the domain, assesses if the site appears on any blacklists, and offers an option to download the results as a PDF. Additionally, the tool can perform an audit to identify and address technical errors that may harm your site, ensuring a thorough analysis for maintaining its security and integrity.
The tool can assist you by
- Integration with Google Safe Browsing Checker – To detect potential threats.
- Blacklist Verification – Checks if the web resource is listed on any blacklists.
- Security Technical Testing – Identifies and addresses technical errors that impact the site’s security.
Key features of the tool
Unified Dashboard – Provides a comprehensive overview of site metrics.
User-Friendly Interface – Ensures easy navigation and usability for users of all expertise levels.
Complete SEO Toolset – Offers an extensive range of SEO tools for keyword research, site audits, and more, aimed at improving website performance and search engine visibility.
How to Use the Tool
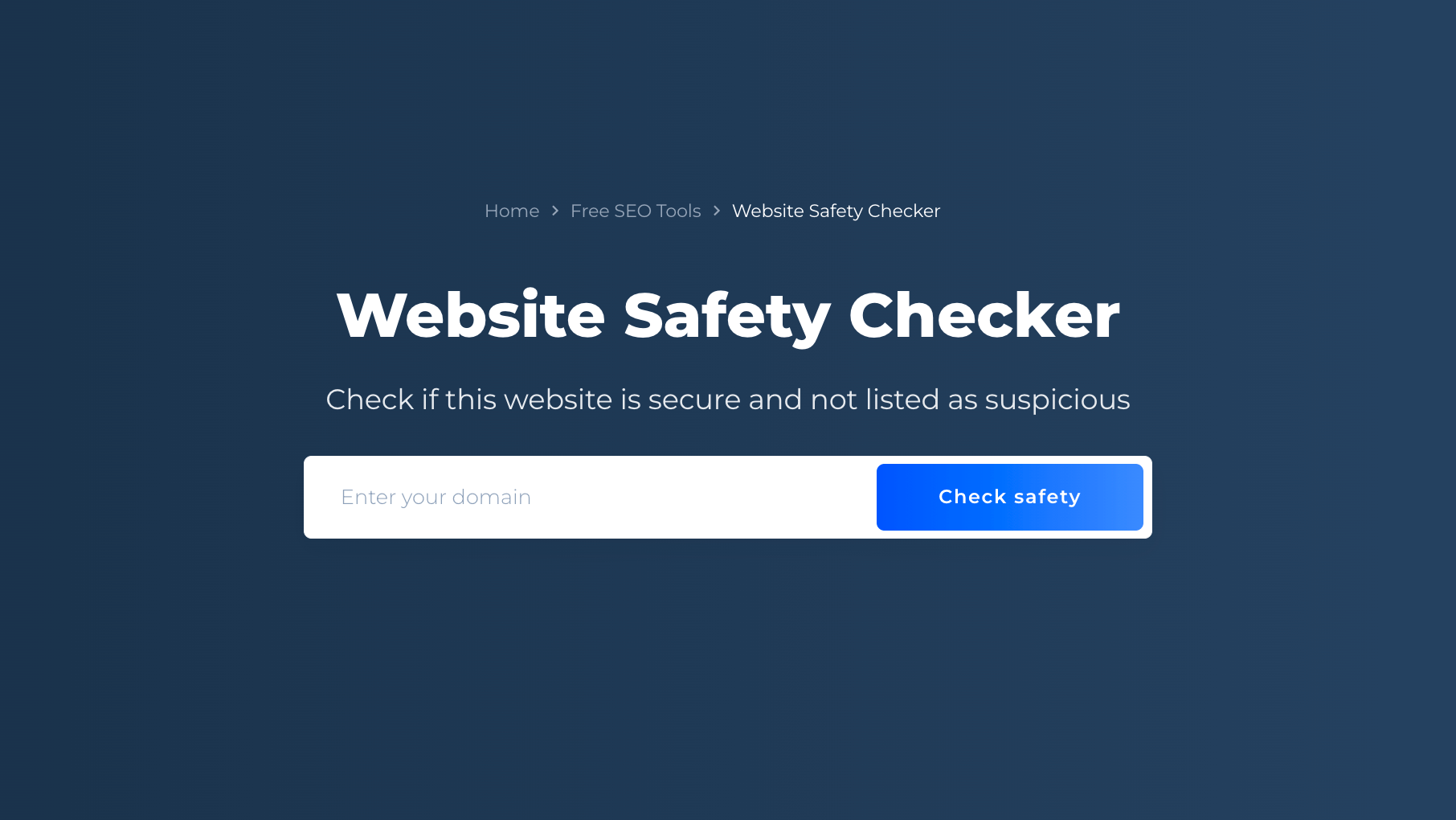
Step 1: To initiate the check website safety, simply input your domain’s URL and click on the “Check Safety” button
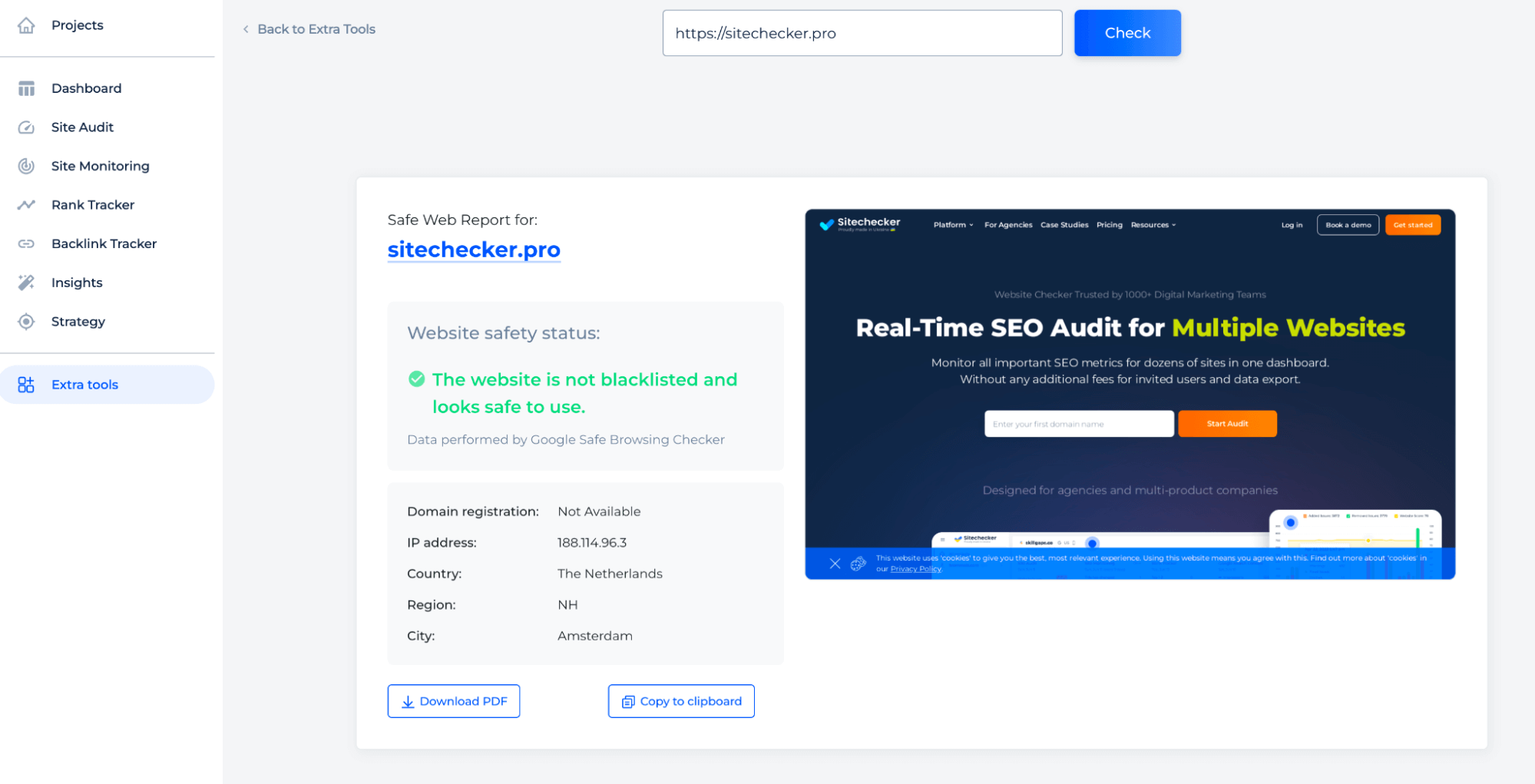
Step 2: Get the result
The Website Safety Checker is a robust tool designed to assess the security of sites. Users can enter a site’s URL into the interface to perform a safety check, which will reveal whether the site is blacklisted or safe to use, based on Google Safe Browsing data. The tool also provides key details like domain registration status, IP address, and geographic location, with options to download the report or copy its details.
Additional features
The tool provides a detailed assessment of your site’s security features. For a hands-on experience, you can initiate a free trial by selecting the appropriate button located at the bottom left of the results interface.
The Google Website Safety Checker showcases an organized dashboard with various sections, such as “Issues list” and “Affected pages by category,” providing a detailed analysis of site performance and security. This includes the number of critical issues, warnings, and opportunities for improvement.
The “Security” section highlights specific vulnerabilities, like pages with internal links to HTTP or missing defenses against common web attacks. For deeper analysis of your site’s directory structure, the Directory Scanner feature can be used to examine all directories and files for potential security risks or outdated protocols.
Incorporating Defacement Monitoring quickly detects unauthorized changes to your website, helping you address security threats and maintain site integrity, performance, and user trust.
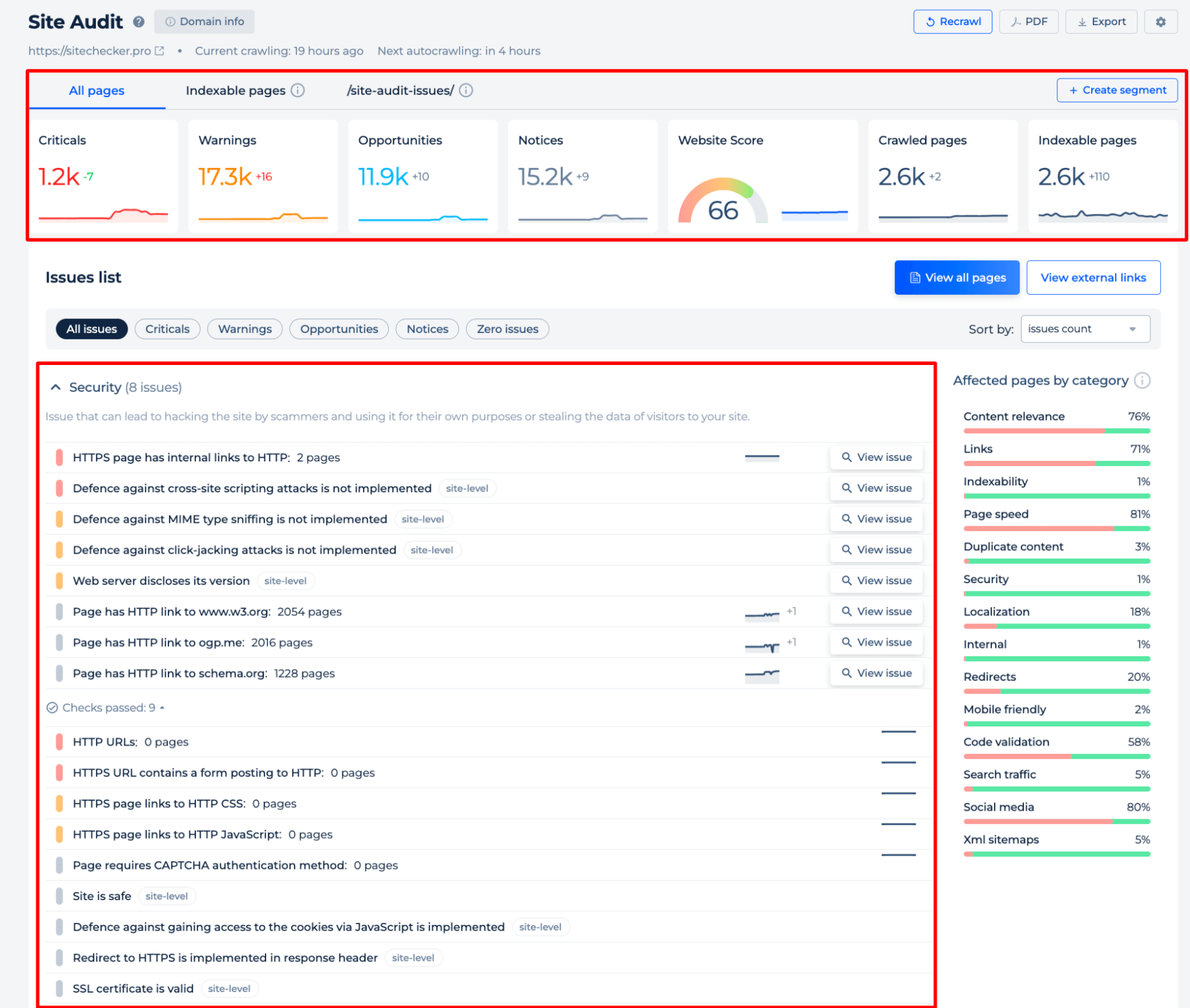
Additionally, to ensure your site is running efficiently, using a Website Speed Test will help you assess load times and pinpoint areas for improvement. There’s also a visual representation of the website score and a categorization of issues that affect different aspects of website health, such as content relevance, page speed, and security.
Final Idea
The Website Safety Checker by Sitechecker is a multifaceted tool that ensures site security through Google Safe Browsing checks, blacklist verification, and a detailed audit for technical vulnerabilities. It features a user-friendly interface with a unified dashboard and a comprehensive SEO toolkit to enhance website performance. To complement this, using a Googlebot Simulator can provide insights into how Google’s crawler navigates your site, ensuring that there are no hidden issues that could impact crawling or indexing. Together, these tools offer a complete solution for optimizing and securing your website’s performance.