Proxy means “usage on behalf of someone else”. But how does it explain the meaning of proxy server? Does it mean that this kind of servers is a tool for hackers? How does a proxy server work and why does anyone need this? Let’s figure it out.
Meaning of Proxy Server
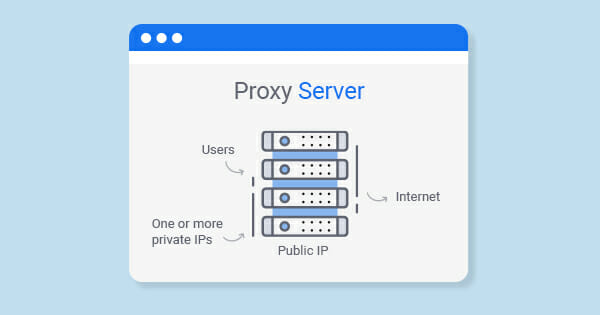
What is a proxy server? That’s not malware so don’t be suspicious with “is this website safe” when some websites use proxies; that’s a special computer that hides your unique IP address granting anonymity. Here is a simple example.
Some streaming services like Netflix don’t work in every country. If you open it, you will get an access error: a message that a service is not available in your country. But how does it know where you are at this moment? With every request to a web service, you share some personal information, including your location. If it doesn’t meet any requirements, a page is not available.
Let’s imagine there is a special provider located in a place where Netflix works. Such an agent is known as proxy. Thousands of those function all over the globe, letting pass your address for located in a different place and help in complicated circumstances.
What is Its Purpose for SEO?
SEO specialists use proxy servers to circumvent restrictions for programs sending bulk requests to search and statistical systems.
For examples, when creating a semantic core, researchers collect variants of words and word combinations that characterize an offer on the website. They check requests users enter in Google when looking for particular things and sites that provide them. A draft of such list can feature thousands of requests. To receive the relevant final list, all results should be parsed, including data from competitors, voice search, statistics services like Ahrefs, SEMrush, etc. Some of them restrict the amount of data one IP can access. This is the moment to consider using proxy – cheap and effective solution. The same happens when parsing site positions for mass verification of SEO-indicators.
Another case of SEO proxies use is submitting articles. In this situation, anonymity and number of proxies are extremely significant, since captcha services block IP on a too big number of requests as well.
When are Proxy Services Used?
- Providing web access from computers on the local network.
- Outsmarting services and getting access to web resources that don’t function in a particular region.
- Data caching: if users often access the same external resources, keep a copy on the server and issue it on request, reducing the load and speeding up the access to the requested information.
- Data compression: a server downloads information from the Internet and transmits it to a user in a compressed form, saving external traffic.
- Protecting local networks by external access limitation: local computers will access external public resources only through this server, and external computers won’t be able at all.
- Restricting outside access from a private network: deny access to certain websites, limit the use of the Internet to some local users, set quotas for traffic or bandwidth, filter ads and viruses.
- Anonymous access: you can hide information about request sources or users, displaying only server data.
- Protects clients’ computers from some DDOS attacks.
The Most Common Types of Proxy Servers
Proxy servers act as intermediaries between client applications (e.g., web browsers) and target servers, providing a variety of functions such as content filtering, performance enhancement, or security and privacy benefits. Here are several types of proxy servers:
| Forward Proxy | This is the most commonly thought-of type when people mention a proxy server. Clients send requests to the forward proxy, which then forwards the request to the destination server. It helps in controlling and monitoring outbound web access and can provide content filtering, regional restrictions, or performance enhancements. |
| Reverse Proxy | It stands in front of one or several servers and optimizes content retrieval for clients. It can handle tasks like load balancing, caching, and SSL encryption. Clients interact with the reverse proxy, which sends requests to the appropriate server. |
| Open Proxy | This type of proxy is accessible by any internet user. It can be subdivided into: – Anonymous Proxy: Hides the user’s IP address from the target server. – Transparent Proxy: This proxy declares that it’s a proxy and passes the user’s IP address to the target server. It doesn’t provide anonymity but can be used for caching or content filtering. – Data Center Proxy: These are private proxies that are not affiliated with an Internet Service Provider (ISP). They come from a secondary corporation and provide you with entirely private IP authentication and high anonymity. |
| Residential Proxy | Uses IP addresses provided by ISPs to homeowners. These proxies offer higher anonymity since they appear as regular users connecting from homes. |
| Content Filtering Proxy | Mainly used in businesses and schools, these proxies block access to certain websites or content. They can also be used to monitor web activity. |
| CGI Proxy | A type of proxy server that allows a user to access web pages or other resources through a website. |
| Caching Proxy | These are used to speed up web browsing by caching (storing) recent or frequent web requests/content, so subsequent requests for the same content can be served more quickly. |
| Transparent Proxy | This is a server that sits between the client and the internet and redirects requests and responses without modifying them. Users are typically unaware of its presence. |
| SOCKS Proxy | Unlike traditional proxies, which interpret and display the data they handle, SOCKS proxies simply transfer data between the client and the server without inspecting it. This makes them versatile and able to handle various types of traffic, including email, FTP, and torrents. |
| Web Proxy | Specifically designed for web content, these proxy servers store web data and are commonly used to provide internet access in places with content restrictions or to save bandwidth by caching popular content. |
Different proxy servers serve various purposes, and the right type to use largely depends on the specific needs of the user or organization.
Reasons You Should Use a Proxy Aerver
There are a lot of cases you may use it properly. But we decided to distinguish the most important of them. According to these 3 reasons you can set up your website and get benefits.
Anonymity
You can hide an IP address, so your current location becomes invisible to other network members. Just be careful: proxy search engine owner completely controls your session – can record all your messages and manipulate web content.
Caching
As you know, there are a lot of different caching types exist. It can be google cache, website cache or proxy caching. Cashed data speeds up the processing of repeated requests. If a client regularly requests the same Word document, get it directly from the server instead of connecting to the target one. And if you were curious what is HTTP proxy, the HTTP protocol is responsible for this, saving server bandwidth and therefore the company’s money.
Filtering
Proxy servers can use filters to evaluate incoming requests, letting you skip only certain types of requests. This feature is most frequently applied for corporate networks.
Why Can Free Proxy Servers be Dangerous?
This solution greatly facilitates the lives of those, who use the Internet actively, bypassing certain prohibitions and removing restrictions. But potential pitfalls hide behind the seeming security, and they shouldn’t be ignored.
But let’s get back to the proxy definition. It is a gateway in a network with a specific IP address located in some region. You register the IP address of a specific proxy in your browser and access a web resource. Data travels to the address on this server, reaches a destination website, then goes back the same way.
If there is no padlock icon that stands for SSL cer protocol in a web address, you cannot be certain that this connection is secure. That’s when you are to answer a question: what’s on its owner’s mind? Variants can be different:
- Collecting data about your PC – browser version, software details, location, etc.
- Packet spoofing that forces transferring additional data.
- Emulation of actions on the website that may compromise a user.
- Gathering passwords, payment details, and other private
- Installing malware, running scripts, etc.
- Further use of infected PCs in DDOS attacks.
A harmless desire to protect yourself from unauthorized control or bypass some bans can have unpredictable consequences. The most interesting thing is that a user doesn’t notice all the actions that occur on their computer. Proxy server opens new opportunities, but users should be careful in order to avoid data leakage and malware attacks.
Check DNS Records for Any Website With DNS Lookup by Sitechecker
The DNS Lookup tool by SiteChecker is a robust utility designed to provide detailed insights into the DNS records of any given domain. This tool is an essential asset for webmasters and SEO professionals, as it allows them to effortlessly check and verify the DNS settings of a website. By simply entering a domain name, users can access a comprehensive display of DNS records, including A, AAAA, MX, NS, and TXT records. This immediate access to DNS information is crucial for troubleshooting domain-related issues and ensuring that a website’s DNS configuration is optimized for both performance and security.

In addition to basic DNS record retrieval, the DNS Lookup tool offers several advanced features. It allows users to inspect specific DNS record types, delve into the configuration details, and even identify potential issues that might affect a website’s accessibility or performance. Furthermore, this tool is invaluable for tracking changes in DNS records over time, providing insights that can help in monitoring domain migrations, server changes, or updates in email configurations. With its user-friendly interface and detailed results, the DNS Lookup tool is an indispensable resource for maintaining a healthy and well-functioning website.
Instant DNS Insight, One Click Away!
Our DNS Lookup tool offers a clear, detailed snapshot of all associated DNS records.
Conclusion
Proxy servers offer anonymity and access to geo-blocked content by masking your IP address, making them essential for accessing a wider range of online services. They are also crucial in SEO for tasks like keyword research and competitive analysis, helping to manage large data requests without triggering search engine restrictions.
The DNS Lookup tool by SiteChecker is indispensable for website management, offering detailed insights into a domain’s DNS records. It assists in troubleshooting, ensuring optimal DNS configurations, and is particularly useful for tracking changes over time during domain migrations or server updates, ensuring a website’s smooth operation and robust online presence.