What is a Host?
The term “host” is a foundational concept that lies at the heart of digital communication and information sharing. But what precisely is a host, and why is it so significant in the world of technology?
At its core, a host refers to any device, computer, or system that plays a pivotal role in providing services, resources, or data to other devices on a network. Think of a host as the digital host or custodian that welcomes and serves information to other devices, often referred to as “clients.”
Hosts are essential components in the functioning of the internet, intranets, and various other types of networks. They serve as the central points of access, ensuring that data can flow seamlessly between devices, whether they are all computer connected, located across the room or on opposite sides of the globe.
To put it simply, a host can be any device with an IP address, from traditional physical servers to virtual machines and even cloud-based instances. These hosts house websites, applications, databases, and an array of digital resources, making them accessible to users and other devices.
Understanding the concept of a host is fundamental to grasping the intricacies of modern computing and networking. In the following chapters, we’ll delve deeper into the various types of IT hosts, their roles, and how they shape the digital landscape. Whether you’re a newcomer to the world of technology or a seasoned IT professional, the concept of a host is a cornerstone of knowledge that will serve you well in your exploration of the digital realm.
Key Components
Understanding the concept of a host in computing is just the beginning. To gain a deeper insight into how hosts function and contribute to the digital world, it’s crucial to explore their key components. These components are the building blocks that make hosts work seamlessly and effectively. In this chapter, we will dissect the essential elements that constitute a host computer’s architecture.
1. Hardware
At the heart of every host lies its hardware. This encompasses the different physical location and components that make up the device or server. Key hardware components of a host may include:
- Central Processing Unit (CPU): The CPU is the brain of the host, responsible for executing instructions and performing calculations.
- Memory (RAM): RAM (Random Access Memory) provides temporary storage for data and instructions that the CPU needs to access quickly.
- Storage Devices: Hard drives, solid-state drives (SSDs), or other storage devices store data and programs.
- Network Interface Card (NIC): The NIC allows the host to connect to a network, enabling communication with other devices.
2. Software
A host computer’s software plays a critical role in its operation. This software includes:
- Operating System: The host’s operating system manages hardware resources, runs applications, and provides a user interface.
- Networking Software: Networking protocols and services facilitate communication with other devices over a network.
- Application Software: Applications and services hosted on the device, such as web servers, email servers, and databases, enable specific functions.
3. Network Configuration
Configuring a host’s network settings is essential for its functionality. Key network configuration components include:
- IP Address: Every host on a network is identified by its unique IP address, allowing data to be routed to the correct destination.
- Subnet Mask: The subnet mask determines the range of IP addresses within a network.
- Gateway: The gateway is the device responsible for routing traffic between the host and other networks or the internet.
4. Security Measures
Securing how cloud hosts operate is paramount in today’s interconnected world. Key security components include:
- Firewalls: Firewalls protect hosts from unauthorized access and cyber threats by filtering incoming and outgoing traffic.
- Authentication and Access Control: Usernames, passwords, and access control lists (ACLs) ensure that only authorized users can interact with the host.
- Encryption: Encrypting data in transit and at rest safeguards sensitive information from eavesdropping and unauthorized access.
Understanding these key components is essential for effectively managing and maintaining hosts in various computing environments. Whether you’re a system administrator, a network engineer, or simply curious about the inner workings of technology, this knowledge provides a solid foundation for comprehending the role of hosts in the digital landscape.
In the following chapters, we’ll explore the distinctions between hosts and servers, delve into different types of hosts, and examine their practical applications in the world of IT.
Host vs Server
In the realm of computing and networking, the terms “host” and “server” are often used interchangeably, but they represent distinct concepts with different roles and functionalities. In this chapter, we’ll explore the differences between a host and a server to shed light on their respective purposes in the digital landscape.
Host: The Versatile Custodian
A host, as previously discussed, is a device, network identity or system that plays a central role in facilitating communication and providing services across a network. Key characteristics of a host include:
- Resource Sharing: Hosts are responsible for hosting resources such as websites, databases, or files, making them accessible to other devices on the network.
- Two-Way Communication: Hosts engage in bidirectional communication, both sending and receiving data. They can act as clients and servers, depending on the context.
- Diverse Types: Hosts come in various forms, including physical servers, virtual machines, and cloud instances. They adapt to the specific needs of different computing environments.
Server: The Specialized Provider
A server, on the other hand, is a specific type of host with a distinct purpose. Servers are designed primarily to provide services, resources, or data to other devices or clients on a network. Key characteristics of a server include:
- Service Delivery: Servers are dedicated to offering specific services, such as web hosting, email, file storage, or database management.
- One-Way Communication: Servers primarily engage in one-way communication, responding to requests from clients and delivering requested data or services.
- Specialized Hardware and Software: Servers often feature specialized hardware configurations and software optimized for their intended service.
Differentiating Hosts and Servers
To differentiate hosts from servers, consider the following:
- Roles: Hosts have a broader range of roles, including hosting services and resources, while servers are specialized in service delivery.
- Functionality: Hosts can act as both clients and servers, handling two-way communication. Servers primarily provide services and respond to client requests.
- Configuration: Hosts are versatile and adaptable, often used in various roles within a network. Servers are configured for specific service delivery.
Understanding the distinctions between hosts and servers is crucial for effectively designing and managing network infrastructures. Whether you’re an IT professional or a curious enthusiast, this knowledge empowers you to make informed decisions about the deployment of devices in your computing environment.
In the subsequent chapters, we’ll delve deeper into the various types of hosts, their functions, and practical applications in IT environments.
Types of Hosts
In the diverse landscape of computing and networking, hosts come in various forms, each tailored to specific functions and environments. Understanding the different types of hosts is essential for navigating the digital world effectively. In this chapter, we’ll explore several common types of network hosts, shedding light on their roles and significance.
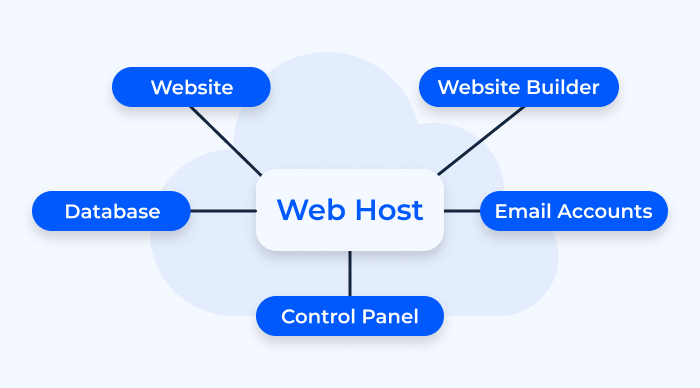
Web Host
Web hosts are the backbone of the internet. They are specialized hosts designed to store and serve websites to users worldwide. Web hosting providers offer various hosting solutions, including shared hosting, virtual private servers (VPS), and dedicated hosting, catering to the needs of websites of all sizes.
Web hosts handle the storage of website files, databases, and other resources, ensuring that webpages are accessible 24/7. Whether you’re running a personal blog or managing a corporate website, web hosts are instrumental in making your online presence a reality.
Cloud Host
Cloud hosts have revolutionized the way we deploy and manage computing resources. These hosts are part of cloud computing platforms and offer scalable, on-demand resources such as virtual machines, storage, and services. Cloud hosts provide flexibility, cost-efficiency, and the ability to adapt to changing workloads, making them a staple in modern IT infrastructure.
Whether you’re building a new application, storing massive amounts of data, or running complex computations, cloud hosts provide the agility and scalability required to meet your needs.
Virtual Host
Virtual hosts, often referred to as virtual hosting or virtual servers, allow multiple websites or services that run multiple domains to coexist on a single physical server. They are a cost-effective solution that maximizes resource utilization. Each virtual host operates as if it has its dedicated server, with its own set of configurations and resources.
Virtual hosts are commonly used in shared hosting environments, where numerous websites share the same server’s resources. They offer a balance between cost efficiency and resource isolation.
Remote Host
Remote hosts are devices or systems that are located at a distance from the user or controlling system. They allow users to access and control remote resources over a network or the internet. Common examples of other hosts include remote servers, virtual private networks (VPNs), and remote desktops.
Remote hosts enable tasks like remote administration, data access, and secure communication across geographical boundaries. They are indispensable in today’s interconnected world.
Host Virtual Machine
Host virtual machines are virtualized instances of a physical host’s operating system and resources. They enable the efficient utilization of hardware by running multiple virtual machines on a single physical host. Virtualization technologies like VMware, Hyper-V, and KVM make host virtual machines possible.
Host virtual machines are fundamental in data centers, enabling the consolidation of servers, resource isolation, and the rapid deployment of new virtual environments.
Mainframe Computer Environments
Mainframes are a class of high-performance computers designed for heavy-duty computing tasks. These environments typically host large-scale applications, databases, and mission-critical workloads. Mainframes are known for their reliability, scalability, and robust security features.
Mainframe computer environments are prevalent in industries such as finance, healthcare, and government, where processing large volumes of data with high precision is essential.
Hostname
The concept of a server’s hostname is a fundamental element in networking. It serves as the human-readable label associated with a host’s IP address, making it easier to identify and locate devices on a network or the internet. Hostnames are integral to domain name system (DNS) resolution and network management.
Understanding how to assign and manage hostnames is crucial for network administrators and anyone involved in configuring and maintaining networked devices.
These are just a few examples of the diverse array of hosts that play pivotal roles in computing and networking. Each type of host serves a unique purpose, contributing to the functionality and interconnectedness of the digital world.
In the following chapters, we will delve deeper into the practical applications of these hosts, exploring how they are used in various computing environments.
Find Out Who is Hosting Any Website with Website Hosting Checker
The Website Hosting Checker by SiteChecker is an efficient and user-friendly tool designed to unveil the hosting provider of any given website. This is crucial for webmasters and digital marketers who need to assess hosting reliability or for those looking to find the hosting providers of their competitors. With a simple interface, the tool requires just a URL to deliver accurate results, demystifying where one or more websites are hosted and aiding in strategic decision-making.
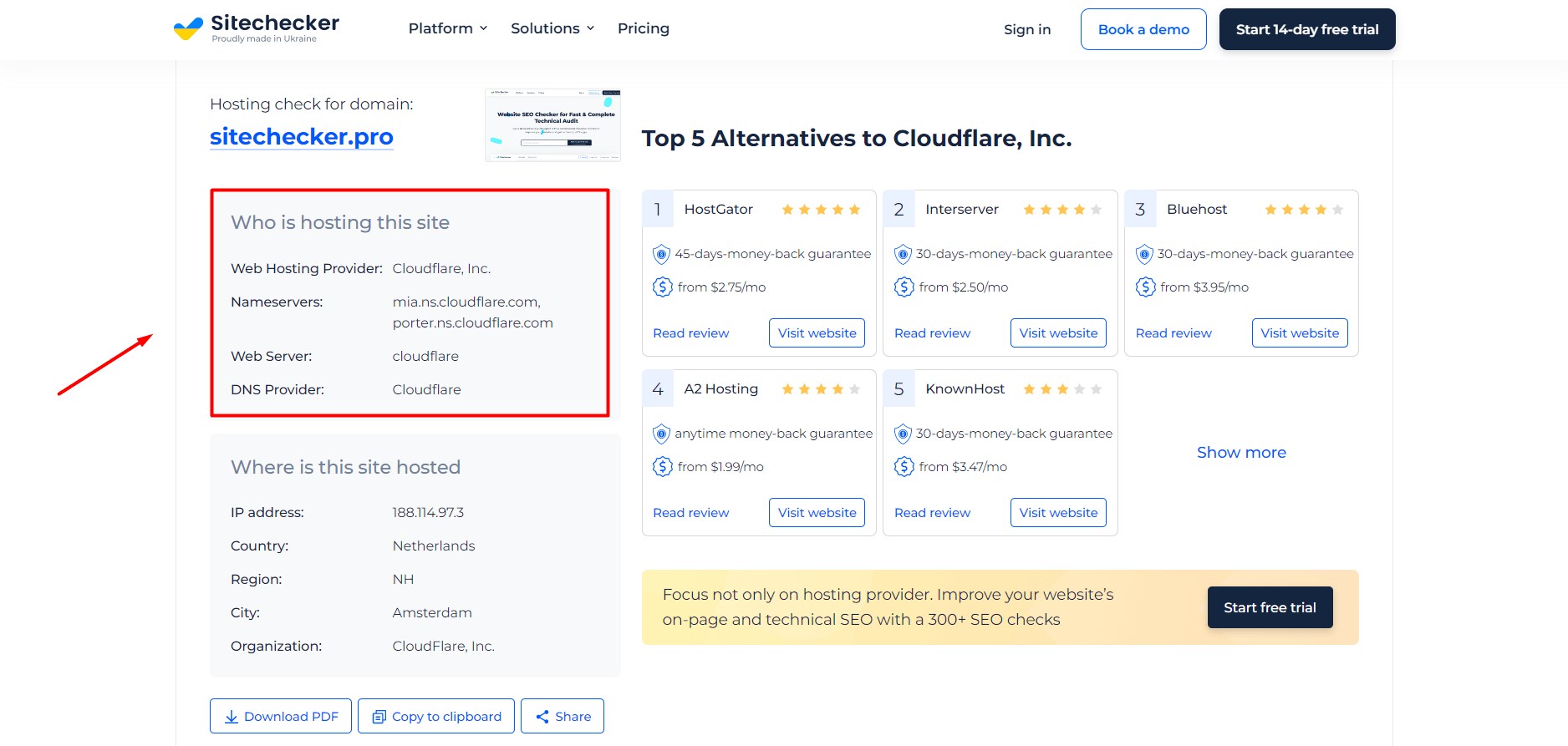
Beyond identifying the hosting service provider, the Website Hosting Checker also furnishes additional details such as the server IP address, the country of the server, and other domains hosted on the same server, which can be valuable for SEO and marketing analysis. For users concerned with privacy, security, or seeking to optimize their own hosting solutions, this tool provides a depth of insight with minimal effort, proving to be an invaluable asset in the web services toolkit.
Reveal the Hosting Behind Any Website!
Our Website Hosting Checker delivers the intel you need with just one click.
Conclusion
Hosts, in all their diverse forms, are the backbone of our digital world. They enable data flow, power services, and shape our connected experiences. Understanding their roles, components, and distinctions is fundamental in navigating the ever-evolving landscape of technology. In a world increasingly defined by connectivity, hosts remain at the core of our digital journey.